Learn
At CheckOut, we prioritize traditional and robust web development processes. Our scalable and resilient server network is powered by a classic stack of nginx, Varnish, and Node.js. For enhanced security, we use a non-Cloudflare security proxy to protect against DDoS attacks.
We avoid modern frameworks and technologies, focusing instead on proven, reliable methods. By not using serverless solutions, we maintain greater control over our infrastructure, ensuring better stability and performance. This traditional approach allows us to deliver consistent and secure services, minimizing the risk of downtime and technical issues.
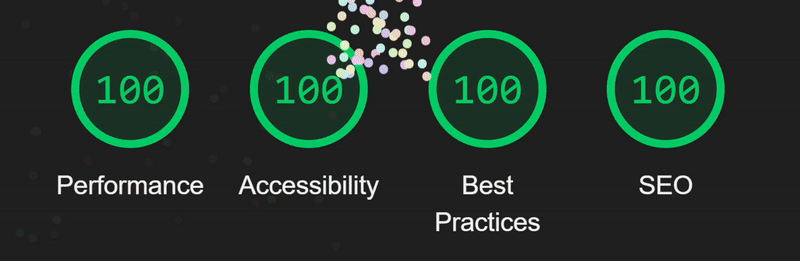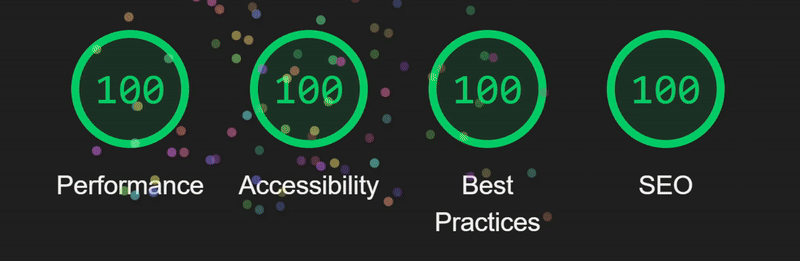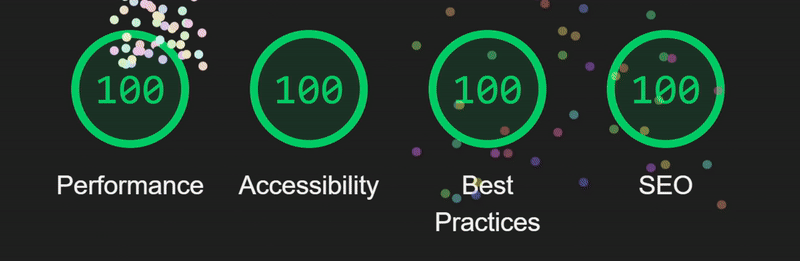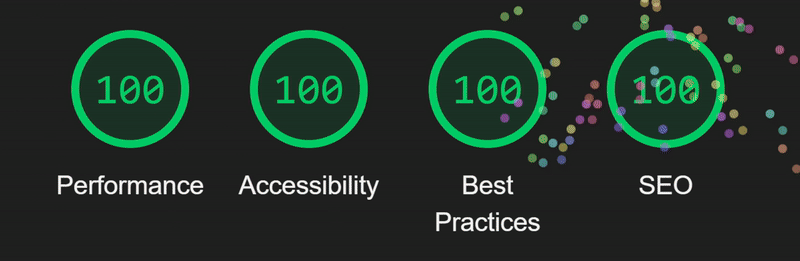
Pictured above is the lighthouse score for CheckOut.
We use a combination of your IP address, account information, and device ID (stored in a cookie) to identify and track your activity on our site, including submissions. This tracking system helps us build your reputation and enhance account functionality, ensuring a personalized and secure experience.
Please note that only logged-in users can access their settings page and manage their account information. For more control over your data, visit our Data Control page where you can reset and delete your information, and request a copy of any data we hold about you.
Displayed in the footer of the account and settings page, your device ID is linked to the cookie that CheckOut stores in your browser or mobile device, which is essential for reputation building and account functionality.
More information is available in the Terms and Privacy policy.
For performance reasons and to ensure the best user experience, especially during busy times, API and code results are hard-cached. This means the cache cannot be manually refreshed by users. However, data should not be delayed by more than a minute, and in normal use, the data displayed on the home page, for example, is updated almost instantaneously.
Please note that caching does not affect AutoCheckin users, as their check-ins are processed instantly on the server-side.
We are pleased to offer a RESTful API for your use. While our site is accessible to anonymous users (please refer to the FAQ section below for details on account requirements), anyone can utilize the API to retrieve data on codes, courses, classes, and other structured information related to our platform. You can explore all the available features in our API explorer.
Please note that CheckOut's API is governed by fair use policies. Along with adhering to our terms of service, it's important not to use the API in ways that could negatively impact other users' experiences. This includes avoiding excessive data requests for timetables and refraining from actions like updating account information or attempting to bypass the cache. Submission of codes via the API is prohibited. Only applications that have received prior approval are permitted to submit codes through the API. To submit codes, please use the web forms available on our web and mobile applications. For more details, visit our API explorer.
We understand that many users value open-source software for its transparency and collaborative potential. However, our website and mobile apps are not currently open source, and there are two main reasons for this:
- Codebase Readiness: While we appreciate the benefits of collaborative development, our codebase is not yet in a state that meets modern development standards. Bringing it up to those standards would require significant time and effort, which we believe is better spent on developing new features and improving the user experience. We are committed to delivering high-quality updates and innovations, and this focus ensures we can continue to meet the needs of our users.
- Security Concerns: Protecting our users is a top priority. Some of the algorithms we use, particularly those designed to combat spam and manage external services, are kept confidential to enhance security. By keeping these aspects of our system closed-source, we reduce the risk of malicious actors exploiting vulnerabilities, ensuring a safer and more reliable experience for everyone.
We hope this clarifies our approach and the reasons behind our decision. We remain committed to transparency where it counts and to delivering a secure, high-quality service for all users.